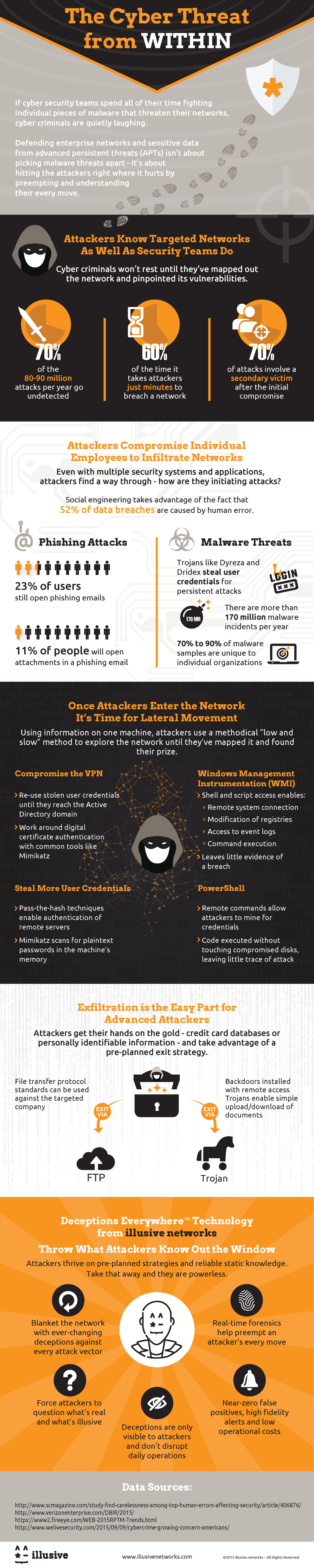
As data breaches become increasingly common, it’s clear that current cyber security methods aren’t working as well as they should, and that a new approach is required to combat cyber threats. For a detailed look at the methods used by cyber attackers to successfully infiltrate networks and extract confidential data, check out the following infographic.
[Click image for full size version]