Internet Infographics
4 Biggest Cyber Threats To UK Businesses
In an ever increasingly digital world, the threat digital attacks pose to businesses of all sizes continues to grow. According to a recent survey by the Department for Digital, Culture, Media and Sport, over four in ten businesses (43%) and two in ten charities (19%) experienced a cybersecurity breach or attack in the last 12 months. These figures demonstrate how important it is for businesses to implement robust security measures that will safeguard key business data.
7 Effective Ways to Protect Your Business From Ransomware Attacks
Ransomware, which was once a buzzword, has now become a major security threat for businesses around the globe. From making their data inaccessible to costing millions of dollars annually, ransomware has forced both businesses and security professionals to take it seriously. Here is an infographic that tells you why your business should seriously consider ransomware attack protection.
The 4 Most Common Lures of Phishing Attacks
This infographic from Inspired eLearning covers the most common types of phishing attacks. Whether its through email, phone call, text message, or USB baiting, learn about how these attacks can occur, common statistics, and prevention tips.
A Look at Internet Censorship Around the World
Censorship looks different depending on the country you are in. Some restrictions are only placed on torrents, but in North Korea, people are prohibited access to political media, pornography, social media, and torrents. While others prohibit access to pornography and restrict political media, social media, and torrents. To better understand censorship, check out the following infographic.
Cyber Security Stats of 21st Century – Cost of Data Breaches
Cybersecurity threats are lurking worldwide, and even the world’s leading companies are not safe from it. Insights show that hacking and online privacy breaches are increasing at an alarming rate. There are pieces of evidence that credentials are sold and bought on the dark web; it is crucial to stay protected and vigilant when using the internet.
How to Disappear From the Internet Completely
Do you long for days gone by, when our lives were led in the real world rather than online? Or possibly you’re unhappy with the way social media makes you feel. Perhaps you’d just like your life to be more private than it is right now. Maybe it’s time for you to disappear from the internet. Completely. Here is a step-by-step guide on how to perform an impressive vanishing act on the Internet.
30 Years of the World Wide Web
March 12th 2019 celebrates 30 years of the history of the web. From the first web page to the way humans connect, communicate, spend and live their everyday lives, the team at AppInstitute takes a look at the major events that have shaped our lives over the past 30 years.
Microsoft Azure- The Perks of Being a Super Cloud
Formerly known as Windows Azure, Microsoft Azure is the premiere flagship cloud computing service from the technology giant. Microsoft gives you many options to use the platform and the different directories you acquire from choosing the Azure platform. Among the options, you get access to exist the choice of working under a scheme of Infrastructure as a Service (IaaS), Product as a Service (PaaS), and Software as a Service (SaaS).
Who Has The Fastest and Slowest Internet in the World?
The need for a faster Internet connection is not a luxury anymore – it’s a basic need. Which country in the world has the fastest internet? If your bet is on the USA, then you are wrong. Users assume the most developed nations have the fastest speeds but this infographic will prove you wrong with exciting facts and figures.
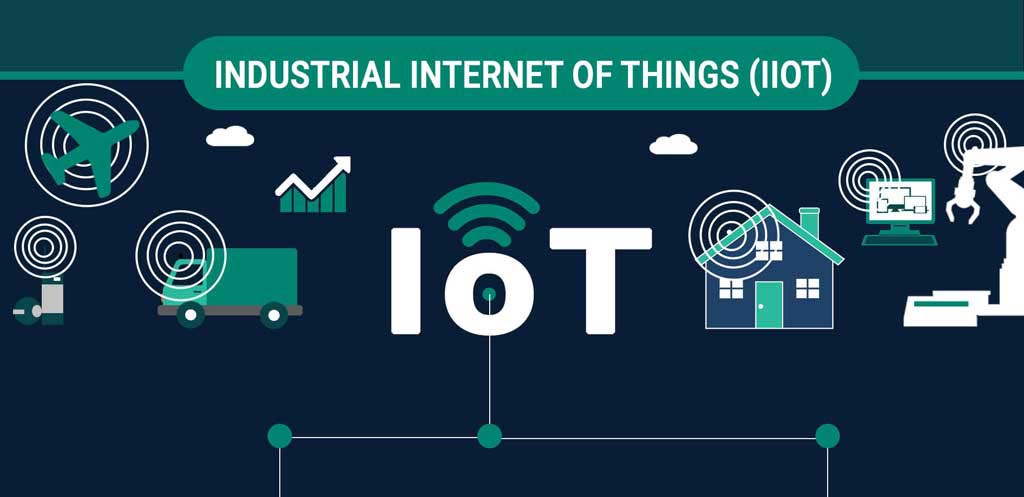
How Industries Are Leveraging the Industrial IoT Potential
Industrial IoT Solutions has bridged the gap between the industrial equipment and the recent technologies that have boomed the market. It has helped many customers to optimize their industrial operations and henceforth increase their productivity and efficiency. Many people have started using Industrial IoT applications for predictive quality and maintenance so that they can remotely monitor their operations from anywhere.
4 Biggest Cyber Threats To UK Businesses
In an ever increasingly digital world, the threat digital attacks pose to businesses of all sizes continues to grow. According to a recent survey by the Department for Digital, Culture, Media and Sport, over four in ten businesses (43%) and two in ten charities (19%) experienced a cybersecurity breach or attack in the last 12 months. These figures demonstrate how important it is for businesses to implement robust security measures that will safeguard key business data.
7 Effective Ways to Protect Your Business From Ransomware Attacks
Ransomware, which was once a buzzword, has now become a major security threat for businesses around the globe. From making their data inaccessible to costing millions of dollars annually, ransomware has forced both businesses and security professionals to take it seriously. Here is an infographic that tells you why your business should seriously consider ransomware attack protection.
The 4 Most Common Lures of Phishing Attacks
This infographic from Inspired eLearning covers the most common types of phishing attacks. Whether its through email, phone call, text message, or USB baiting, learn about how these attacks can occur, common statistics, and prevention tips.
A Look at Internet Censorship Around the World
Censorship looks different depending on the country you are in. Some restrictions are only placed on torrents, but in North Korea, people are prohibited access to political media, pornography, social media, and torrents. While others prohibit access to pornography and restrict political media, social media, and torrents. To better understand censorship, check out the following infographic.
Cyber Security Stats of 21st Century – Cost of Data Breaches
Cybersecurity threats are lurking worldwide, and even the world’s leading companies are not safe from it. Insights show that hacking and online privacy breaches are increasing at an alarming rate. There are pieces of evidence that credentials are sold and bought on the dark web; it is crucial to stay protected and vigilant when using the internet.
How to Disappear From the Internet Completely
Do you long for days gone by, when our lives were led in the real world rather than online? Or possibly you’re unhappy with the way social media makes you feel. Perhaps you’d just like your life to be more private than it is right now. Maybe it’s time for you to disappear from the internet. Completely. Here is a step-by-step guide on how to perform an impressive vanishing act on the Internet.
30 Years of the World Wide Web
March 12th 2019 celebrates 30 years of the history of the web. From the first web page to the way humans connect, communicate, spend and live their everyday lives, the team at AppInstitute takes a look at the major events that have shaped our lives over the past 30 years.
Microsoft Azure- The Perks of Being a Super Cloud
Formerly known as Windows Azure, Microsoft Azure is the premiere flagship cloud computing service from the technology giant. Microsoft gives you many options to use the platform and the different directories you acquire from choosing the Azure platform. Among the options, you get access to exist the choice of working under a scheme of Infrastructure as a Service (IaaS), Product as a Service (PaaS), and Software as a Service (SaaS).
Who Has The Fastest and Slowest Internet in the World?
The need for a faster Internet connection is not a luxury anymore – it’s a basic need. Which country in the world has the fastest internet? If your bet is on the USA, then you are wrong. Users assume the most developed nations have the fastest speeds but this infographic will prove you wrong with exciting facts and figures.
How Industries Are Leveraging the Industrial IoT Potential
Industrial IoT Solutions has bridged the gap between the industrial equipment and the recent technologies that have boomed the market. It has helped many customers to optimize their industrial operations and henceforth increase their productivity and efficiency. Many people have started using Industrial IoT applications for predictive quality and maintenance so that they can remotely monitor their operations from anywhere.
Search 12,000+ Infographics!
Partners
Browse Archives By Category
Animated Infographics
Business Infographics
Career & Jobs Infographics
Education Infographics
Entertainment Industry Infographics
Environmental Infographics
Finance & Money Infographics
Food & Drink Infographics
Health Infographics
Historical Infographics
Home & Garden Infographics
Internet Infographics
Law and Legal Infographics
Lifestyle Infographics
Marketing Infographics
Offbeat Infographics
Parenting Infographics
Pets & Animals Infographics
Political Infographics
Shopping Infographics
Sports and Athletic Infographics
Technology Infographics
Transportation Infographics
Travel Infographics
Video Infographics