Technology Infographics
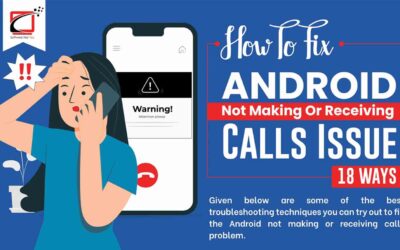
Android Not Making Or Receiving Calls
If you’re an Android user, you may have experienced the problem with your phone not being able to make or receive calls. This can be a major inconvenience, especially if you rely on your phone for work or emergency purposes. Here is a visual that provides more details on what to do when your Android device has these issues.
A Guide on Responding to Data Breaches
Data breaches are one of the biggest cyber threats any organization could encounter, especially since most of them keep records of their customers’ sensitive data. In fact, 2021 saw 4,145 publicly disclosed cases of data breaches, resulting in over 22 billion records being exposed. Here is a visual guide on responding to data breaches.
Knowledge, Possession, and Inherence: A Guide to Authentication Factors
With today’s sophisticated technology come new and inventive ways for fraudsters to access databases. A 45 percent rise over 2019 saw 4.8 million allegations of fraud, identity theft, and other cyber risks submitted to the Federal Trade Commission’s (FTC) Consumer Sentinel Network. Q5id has put together the following infographic which is a guide to authentication factors.
The Increase in Solar Panel Efficiency Over Time
Solar panel efficiency has grown quite a bit since the very first solar cells were created back in the 1880s. Back then, the solar cell efficiency was less than 1%, but today scientists are creating high-efficiency solar panels that can reach almost 50% efficiency. SolarPower.Guide has put together a timeline of solar cell technology and how far it has come since the 1800’s.
What is an NFT?
Here is an infographic that answers the question, “What is an NFT?” It describes what they are, when non-fungible-tokens where created, what they are used for, why are NFTs important, how to buy NFTs, and whether they are safe.
How to Develop a Digital Product – Challenges, Stages and Benefits
In the modern environment, an information technology company’s survival may be risked if it does not digitally transform to match the economic landscape’s needs and expectations. Anblicks has designed the following infographic to address the issues that software firms encounter while enhancing or developing digital products.
What is nopCommerce?
With the growing trend of online shopping, e-commerce platforms are combating it to take that number one spot. nopCommerce is one of those that is competing. It is an open-source CMS platform based on Microsoft’s ASP.NET Core framework and SQL Server backend database. Learn more about nopCommerce in this infographic.
Website Maintenance: The Multifold Aspects You Should Know
Webmasters spend a significant amount of time and money creating a dynamic site for their business. However, the work does not stop there as a web site will need to be maintained. Due to the technical challenges that can be experienced in maintaining a website, one should handle the procedure with extreme care and vigilance.
AWS vs Azure: Battle of the Cloud Giants
Cloud computing is on-demand access, via the internet, to computing resources. The two most popular cloud computing platforms are Amazon Web Services (AWS) and Microsoft Azure. In this infographic we will compare these two cloud giants and see which one is best for your business.
Non-Fungible Tokens (NFTs) Explained
A Non-fungible token, also referred to as “NFT,” is a digital asset portraying real-world objects such as videos, music, art, in-game items, etc. What is the hype around NFTs? Here are the core details of NFTs in this helpful guide, courtesy of Zenesys.
Android Not Making Or Receiving Calls
If you’re an Android user, you may have experienced the problem with your phone not being able to make or receive calls. This can be a major inconvenience, especially if you rely on your phone for work or emergency purposes. Here is a visual that provides more details on what to do when your Android device has these issues.
A Guide on Responding to Data Breaches
Data breaches are one of the biggest cyber threats any organization could encounter, especially since most of them keep records of their customers’ sensitive data. In fact, 2021 saw 4,145 publicly disclosed cases of data breaches, resulting in over 22 billion records being exposed. Here is a visual guide on responding to data breaches.
Knowledge, Possession, and Inherence: A Guide to Authentication Factors
With today’s sophisticated technology come new and inventive ways for fraudsters to access databases. A 45 percent rise over 2019 saw 4.8 million allegations of fraud, identity theft, and other cyber risks submitted to the Federal Trade Commission’s (FTC) Consumer Sentinel Network. Q5id has put together the following infographic which is a guide to authentication factors.
The Increase in Solar Panel Efficiency Over Time
Solar panel efficiency has grown quite a bit since the very first solar cells were created back in the 1880s. Back then, the solar cell efficiency was less than 1%, but today scientists are creating high-efficiency solar panels that can reach almost 50% efficiency. SolarPower.Guide has put together a timeline of solar cell technology and how far it has come since the 1800’s.
What is an NFT?
Here is an infographic that answers the question, “What is an NFT?” It describes what they are, when non-fungible-tokens where created, what they are used for, why are NFTs important, how to buy NFTs, and whether they are safe.
How to Develop a Digital Product – Challenges, Stages and Benefits
In the modern environment, an information technology company’s survival may be risked if it does not digitally transform to match the economic landscape’s needs and expectations. Anblicks has designed the following infographic to address the issues that software firms encounter while enhancing or developing digital products.
What is nopCommerce?
With the growing trend of online shopping, e-commerce platforms are combating it to take that number one spot. nopCommerce is one of those that is competing. It is an open-source CMS platform based on Microsoft’s ASP.NET Core framework and SQL Server backend database. Learn more about nopCommerce in this infographic.
Website Maintenance: The Multifold Aspects You Should Know
Webmasters spend a significant amount of time and money creating a dynamic site for their business. However, the work does not stop there as a web site will need to be maintained. Due to the technical challenges that can be experienced in maintaining a website, one should handle the procedure with extreme care and vigilance.
AWS vs Azure: Battle of the Cloud Giants
Cloud computing is on-demand access, via the internet, to computing resources. The two most popular cloud computing platforms are Amazon Web Services (AWS) and Microsoft Azure. In this infographic we will compare these two cloud giants and see which one is best for your business.
Non-Fungible Tokens (NFTs) Explained
A Non-fungible token, also referred to as “NFT,” is a digital asset portraying real-world objects such as videos, music, art, in-game items, etc. What is the hype around NFTs? Here are the core details of NFTs in this helpful guide, courtesy of Zenesys.
Search 12,000+ Infographics!
Partners
Browse Archives By Category
Animated Infographics
Business Infographics
Career & Jobs Infographics
Education Infographics
Entertainment Industry Infographics
Environmental Infographics
Finance & Money Infographics
Food & Drink Infographics
Health Infographics
Historical Infographics
Home & Garden Infographics
Internet Infographics
Law and Legal Infographics
Lifestyle Infographics
Marketing Infographics
Offbeat Infographics
Parenting Infographics
Pets & Animals Infographics
Political Infographics
Shopping Infographics
Sports and Athletic Infographics
Technology Infographics
Transportation Infographics
Travel Infographics
Video Infographics