Technology Infographics
Ecommerce Update: Technology & Trends in 2022 and Beyond
The COVID-19 global health crisis has pushed the limits of many industries like healthcare, education, entertainment, and even eCommerce. Many of these industries had to step up their game and adapt to a new digital setup. Work setups became remote, the healthcare industry offered telemedicine, and schools conducted online learning.
The Most Significant Events That Have Shaped the NFT Industry
NFT is the biggest hype today. People aren’t apathetic about it especially when it comes to millions of dollars. But before achieving such fame, let’s go to the past of NFT and identify what history it lived until it became today’s most discussed topic. In this infographic, look at the most significant events that have shaped the NFT industry.
Rise of Artificial Intelligence in Call Centers
Emerging tools designed to boost efficiency and customer engagement are gradually transforming the modern call center, helping redefine the customer experience. In this infographic, EB Call Center puts together quick statistics about the benefits of AI and its various applications in the call center industry to help you better understand the nature of this technology.
Statistics on Wearables
More than 70 million people in the US are using wearable technology to improve their day to day lives. From smartwatches to smartphones, smart rings and smart bands. Wearables have become immensely popular in recent years as app developers strive to make them even more usable to the general public.
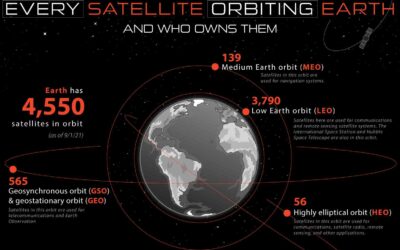
Every Satellite Orbiting Earth and Who Owns Them
As of the writing of this post, there are currently 4,550 satellites orbiting the Earth. Their purposes range from military observation to communications. But which countries and companies are responsible for each of these satellites? This graphic visualizes the companies that are responsible for the most satellites as well as their countries of operations.
Pegasus Spyware 101 and How to Protect Your Information
Over the summer, spyware known as Pegasus made global news when it infected thousands of phones internationally. The targets included journalists, activists and politicians. Consequently, thousands of phone numbers were leaked. In the following infographic, PeopleFinders.com looks at Pegasus Spyware and how to protect your information.
UCaaS vs. VoIP: Which is Better for Your Firm?
You may be searching for a new business phone system, and when you Google “business phone systems,” the millions of various results for terms like “UCaaS,” “VoIP,” and “Cloud Communications” might confuse you. How can you tell the difference between these solutions and which is best for your company? Acefone clarifies the differences between UCaaS and VoIP in the following infographic.
App Development Cost Guide
Mobile app development cost can vary dramatically depending on a number of factors. How much does it cost to develop a mobile app? Which features make the app development cost go up and how do you find the right vendor to save on the service provider charges? DOIT Software has put together the following app development cost guide.
Holiday Tech Shortages
Given the chip shortages, supply chain, and shipping issues, holiday shopping might look a lot different this year. The gift you want to give might be sitting in a drawer and you could give it new life by getting it fixed inexpensively by an expert. Learn more about holiday tech shortages in the infographic below, courtesy of uBreakiFix.
Stopping Ransomware Before it Starts
In today’s world, it appears that cyber attacks and ransomware is an eventuality for your business to have to deal with. But there’s hope! Learn how to you can be proactive in stopping ransomware in the following infographic, courtesy of Cyber Security Degrees.
Ecommerce Update: Technology & Trends in 2022 and Beyond
The COVID-19 global health crisis has pushed the limits of many industries like healthcare, education, entertainment, and even eCommerce. Many of these industries had to step up their game and adapt to a new digital setup. Work setups became remote, the healthcare industry offered telemedicine, and schools conducted online learning.
The Most Significant Events That Have Shaped the NFT Industry
NFT is the biggest hype today. People aren’t apathetic about it especially when it comes to millions of dollars. But before achieving such fame, let’s go to the past of NFT and identify what history it lived until it became today’s most discussed topic. In this infographic, look at the most significant events that have shaped the NFT industry.
Rise of Artificial Intelligence in Call Centers
Emerging tools designed to boost efficiency and customer engagement are gradually transforming the modern call center, helping redefine the customer experience. In this infographic, EB Call Center puts together quick statistics about the benefits of AI and its various applications in the call center industry to help you better understand the nature of this technology.
Statistics on Wearables
More than 70 million people in the US are using wearable technology to improve their day to day lives. From smartwatches to smartphones, smart rings and smart bands. Wearables have become immensely popular in recent years as app developers strive to make them even more usable to the general public.
Every Satellite Orbiting Earth and Who Owns Them
As of the writing of this post, there are currently 4,550 satellites orbiting the Earth. Their purposes range from military observation to communications. But which countries and companies are responsible for each of these satellites? This graphic visualizes the companies that are responsible for the most satellites as well as their countries of operations.
Pegasus Spyware 101 and How to Protect Your Information
Over the summer, spyware known as Pegasus made global news when it infected thousands of phones internationally. The targets included journalists, activists and politicians. Consequently, thousands of phone numbers were leaked. In the following infographic, PeopleFinders.com looks at Pegasus Spyware and how to protect your information.
UCaaS vs. VoIP: Which is Better for Your Firm?
You may be searching for a new business phone system, and when you Google “business phone systems,” the millions of various results for terms like “UCaaS,” “VoIP,” and “Cloud Communications” might confuse you. How can you tell the difference between these solutions and which is best for your company? Acefone clarifies the differences between UCaaS and VoIP in the following infographic.
App Development Cost Guide
Mobile app development cost can vary dramatically depending on a number of factors. How much does it cost to develop a mobile app? Which features make the app development cost go up and how do you find the right vendor to save on the service provider charges? DOIT Software has put together the following app development cost guide.
Holiday Tech Shortages
Given the chip shortages, supply chain, and shipping issues, holiday shopping might look a lot different this year. The gift you want to give might be sitting in a drawer and you could give it new life by getting it fixed inexpensively by an expert. Learn more about holiday tech shortages in the infographic below, courtesy of uBreakiFix.
Stopping Ransomware Before it Starts
In today’s world, it appears that cyber attacks and ransomware is an eventuality for your business to have to deal with. But there’s hope! Learn how to you can be proactive in stopping ransomware in the following infographic, courtesy of Cyber Security Degrees.
Search 12,000+ Infographics!
Partners
Browse Archives By Category
Animated Infographics
Business Infographics
Career & Jobs Infographics
Education Infographics
Entertainment Industry Infographics
Environmental Infographics
Finance & Money Infographics
Food & Drink Infographics
Health Infographics
Historical Infographics
Home & Garden Infographics
Internet Infographics
Law and Legal Infographics
Lifestyle Infographics
Marketing Infographics
Offbeat Infographics
Parenting Infographics
Pets & Animals Infographics
Political Infographics
Shopping Infographics
Sports and Athletic Infographics
Technology Infographics
Transportation Infographics
Travel Infographics
Video Infographics