Technology Infographics
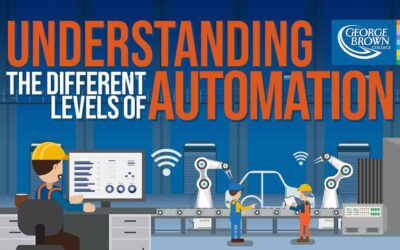
Understanding the Different Levels of Automation
AI is becoming more advanced each coming year, as robotics are improving and factories around the world are becoming increasingly more integrated. With all these industrial advancements constantly in motion, understanding the Levels of Automation is an integral first step for any job within the automation sector. The following infographic looks at the different levels of automation in more detail.
How eCommerce Benefits from Product Configuration
Personalization has been a long touted feature of eCommerce, but using a product configurator – the true technology behind scalable customization makes it possible. Check out this infographic from PARTsolutions for a deep dive for more.
How to Pick the Best WordPress Hosting
Not all website hosting providers are created equal. Many websites run WordPress and speed is such an important factor in the pandemic world we live in. Check out this visual deep dive on how to pick the best WordPress hosting provider.
Ten Software Development Trends for 2020-2021
The Covid-19 pandemic significantly impacted all industries and spheres, including software development. Some new software development trends have been formulated under the influence of new circumstances, for example, the prevailing remote work or increased digitization of businesses. This infographic depicts the top ten software development trends we are going to see in 2021, based on detailed statistics.
Progressive Web Apps: The Superpower You Need to Embrace
Nowadays, customers want it all: they expect a hyper-personalized, engaging and fast web experience anywhere they go. Progressive Web Apps (PWAs) have disrupted the mobile app model by bringing native app functionality to the web. PWAs are a critical factor in website success. Here’s a breakdown of why embracing PWAs pays off and how it can help your business.
Mobile App Development
Here is an infographic from AndroidDevelopers.co that lays out a basic knowledge about app development. It looks at the different types of Apps, what are the different component and factors that influence the cost and more. [Click here for full size version]
Mobile App Statistics You Need to Know in 2020
Whether you are a developer, an app owner, or a marketer, being up to date on the key app stats from the intriguing world of web applications is essential to make sure your own app or future app aligns with what your target audience wants and expects from the mobile apps of the future.
Why You Need to Change Your Approach to Hyper-V Data Protection
Businesses around the world continue to invest in virtualization technologies as they help ensure IT efficiency, increase infrastructure uptime and availability, and cut operational costs. This infographic discusses Microsoft Hyper-V and its unique data protection challenges and how businesses can overcome them with NAKIVO Backup & Replication.
Cybersecurity For The Post-Covid Economy
In the near future, we could see cyberpandemics that spread faster and further than a biological virus, with an equal or greater impact. Will the next pandemic be digital? Find out what Data Connectors has to say on the matter in the following infographic.
Top Mobile Device Cybersecurity Safety Trends to Watch in 2021
As COVID-19 has forced 51% of the U.S. workforce to work from home, mobile devices’ usage has exploded. As a result, international cyber security criminals and rogue host nations are exploiting this opportunity to redirect their attacks for stealing sensitive and private corporate data directly from individual employees’ mobile devices.
Search 11,800+ Infographics!
Partners
Browse Archives By Category
Animated Infographics
Business Infographics
Career & Jobs Infographics
Education Infographics
Entertainment Industry Infographics
Environmental Infographics
Finance & Money Infographics
Food & Drink Infographics
Health Infographics
Historical Infographics
Home & Garden Infographics
Interactive Infographics
Internet Infographics
Law and Legal Infographics
Lifestyle Infographics
Marketing Infographics
Offbeat Infographics
Parenting Infographics
Pets & Animals Infographics
Political Infographics
Shopping Infographics
Sports and Athletic Infographics
Technology Infographics
Transportation Infographics
Travel Infographics
Video Infographics